diff options
Diffstat (limited to 'docs')
| -rw-r--r-- | docs/Changelog.md | 9 | ||||
| -rw-r--r-- | docs/power_schedules.md | 1 |
2 files changed, 6 insertions, 4 deletions
diff --git a/docs/Changelog.md b/docs/Changelog.md index 1fb78625..3eb5d329 100644 --- a/docs/Changelog.md +++ b/docs/Changelog.md @@ -24,10 +24,11 @@ sending a mail to <afl-users+subscribe@googlegroups.com>. - python mutator modules and custom mutator modules now use the same interface and hence the API changed - AFL_AUTORESUME will resume execution without the need to specify `-i -` - - added experimental power schedule -p mmopt that ignores the runtime of - queue entries and gives higher weighting to the last 5 queue entries - it is currently experimental and subject to change but preliminary - results are good + - added experimental power schedules (-p): + - mmopt: ignores runtime of queue entries, gives higher weighting to + the last 5 queue entries + - rare: puts focus on queue entries that hits rare branches, also ignores + runtime - LTO collision free instrumented added in llvm_mode with afl-clang-lto - note that this mode is amazing, but quite some targets won't compile - llvm_mode InsTrim mode: diff --git a/docs/power_schedules.md b/docs/power_schedules.md index cdada0f6..c69c64d2 100644 --- a/docs/power_schedules.md +++ b/docs/power_schedules.md @@ -20,6 +20,7 @@ We find that AFL's exploitation-based constant schedule assigns **too much energ | `-p lin` | 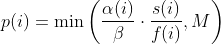 | | `-p exploit` (AFL) | 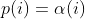 | | `-p mmopt` | Experimental: `explore` with no weighting to runtime and increased weighting on the last 5 queue entries | +| `-p rare` | Experimental: `rare` puts focus on queue entries that hit rare edges | where *α(i)* is the performance score that AFL uses to compute for the seed input *i*, *β(i)>1* is a constant, *s(i)* is the number of times that seed *i* has been chosen from the queue, *f(i)* is the number of generated inputs that exercise the same path as seed *i*, and *μ* is the average number of generated inputs exercising a path. More details can be found in the paper that was accepted at the [23rd ACM Conference on Computer and Communications Security (CCS'16)](https://www.sigsac.org/ccs/CCS2016/accepted-papers/). |
