diff options
Diffstat (limited to 'docs')
| -rw-r--r-- | docs/Changelog.md | 18 | ||||
| -rw-r--r-- | docs/PATCHES.md | 1 | ||||
| -rw-r--r-- | docs/env_variables.md | 34 | ||||
| -rw-r--r-- | docs/ideas.md | 2 | ||||
| -rw-r--r-- | docs/notes_for_asan.md | 4 | ||||
| -rw-r--r-- | docs/power_schedules.md | 1 | ||||
| -rw-r--r-- | docs/status_screen.md | 52 |
7 files changed, 76 insertions, 36 deletions
diff --git a/docs/Changelog.md b/docs/Changelog.md index e1f3cd7e..6af269ce 100644 --- a/docs/Changelog.md +++ b/docs/Changelog.md @@ -11,21 +11,31 @@ sending a mail to <afl-users+subscribe@googlegroups.com>. ### Version ++2.62d (develop): + ! the repository was moved from vanhauser-thc to AFLplusplus. It is now + an own organisation :) + ! development and acceptance of PRs now happen only in the dev branch + and only occasionally when everything is fine we PR to master - all: - big code changes to make afl-fuzz thread-safe so afl-fuzz can spawn multiple fuzzing threads in the future or even become a library - afl basic tools now report on the environment variables picked up - more tools get environment variable usage info in the help output + - force all output to stdout (some OK/SAY/WARN messages were sent to + stdout, some to stderr) - afl-fuzz: - python mutator modules and custom mutator modules now use the same interface and hence the API changed - AFL_AUTORESUME will resume execution without the need to specify `-i -` - - added experimental power schedule -p mmopt that ignores the runtime of - queue entries and gives higher weighting to the last 5 queue entries - it is currently experimental and subject to change but preliminary - results are good + - added experimental power schedules (-p): + - mmopt: ignores runtime of queue entries, gives higher weighting to + the last 5 queue entries + - rare: puts focus on queue entries that hits rare branches, also ignores + runtime - LTO collision free instrumented added in llvm_mode with afl-clang-lto - note that this mode is amazing, but quite some targets won't compile + - Added llvm_mode NGRAM prev_loc coverage by Adrean Herrera + (https://github.com/adrianherrera/afl-ngram-pass/), activate by setting + AFL_LLVM_NGRAM_SIZE - llvm_mode InsTrim mode: - removed workaround for bug where paths were not instrumented and imported fix by author diff --git a/docs/PATCHES.md b/docs/PATCHES.md index 1dfb6622..a6783523 100644 --- a/docs/PATCHES.md +++ b/docs/PATCHES.md @@ -20,6 +20,7 @@ afl-qemu-speed.diff by abiondo on github afl-qemu-optimize-map.diff by mh(at)mh-sec(dot)de ``` ++ llvm_mode ngram prev_loc coverage (github.com/adrianherrera/afl-ngram-pass) + Custom mutator (native library) (by kyakdan) + unicorn_mode (modernized and updated by domenukk) + instrim (https://github.com/csienslab/instrim) was integrated diff --git a/docs/env_variables.md b/docs/env_variables.md index 8c7510cd..98f27bdf 100644 --- a/docs/env_variables.md +++ b/docs/env_variables.md @@ -93,23 +93,26 @@ Then there are a few specific features that are only available in llvm_mode: ### LTO -This is a different kind way of instrumentation: first it compiles all -code in LTO (link time optimization) and then performs an edge inserting -instrumentation which is 100% collision free (collisions are a big issue -in afl and afl-like instrumentations). This is performed by using -afl-clang-lto/afl-clang-lto++ instead of afl-clang-fast, but is only -built if LLVM 9 or newer is used. - -None of these options are necessary to be used and are rather for manual -use (which only ever the author of this LTO implementation will use ;-) -These are used if several seperated instrumentation are performed which -are then later combined. + This is a different kind way of instrumentation: first it compiles all + code in LTO (link time optimization) and then performs an edge inserting + instrumentation which is 100% collision free (collisions are a big issue + in afl and afl-like instrumentations). This is performed by using + afl-clang-lto/afl-clang-lto++ instead of afl-clang-fast, but is only + built if LLVM 9 or newer is used. + + None of these options are necessary to be used and are rather for manual + use (which only ever the author of this LTO implementation will use ;-) + These are used if several seperated instrumentation are performed which + are then later combined. - AFL_LLVM_LTO_STARTID sets the starting location ID for the instrumentation. This defaults to 1 - AFL_LLVM_LTO_DONTWRITEID prevents that the highest location ID written into the instrumentation is set in a global variable + Instrim, LTO and ngram modes can not be used together. + See llvm_mode/README.LTO.md for more information. + ### LAF-INTEL This great feature will split compares to series of single byte comparisons @@ -149,8 +152,17 @@ are then later combined. functions with a single basic block. This is useful for most C and some C++ targets. + Instrim, LTO and ngram modes can not be used together. See llvm_mode/README.instrim.md +### NGRAM + + - Setting AFL_LLVM_NGRAM_SIZE activates ngram prev_loc coverage, good + values are 2, 4 or 8. + + Instrim, LTO and ngram modes can not be used together. + See llvm_mode/README.ngram.md + ### NOT_ZERO - Setting AFL_LLVM_NOT_ZERO=1 during compilation will use counters diff --git a/docs/ideas.md b/docs/ideas.md index 44dcccb2..686c262d 100644 --- a/docs/ideas.md +++ b/docs/ideas.md @@ -33,7 +33,7 @@ This is an excellent mutations scheduler based on Particle Swarm Optimization but the current implementation schedule only the mutations that were present on AFL. -AFL++ added a lost of optional mutators like the Input-2-State one based +AFL++ added a lot of optional mutators like the Input-2-State one based on Redqueen, the Radamsa mutator, the Custom mutator (the user can define its own mutator) and the work is to generalize MOpt for all the current and future mutators. diff --git a/docs/notes_for_asan.md b/docs/notes_for_asan.md index feac49f9..b65873be 100644 --- a/docs/notes_for_asan.md +++ b/docs/notes_for_asan.md @@ -28,6 +28,10 @@ Note that ASAN is incompatible with -static, so be mindful of that. (You can also use AFL_USE_MSAN=1 to enable MSAN instead.) +NOTE: if you run several slaves only one should run the target compiled with +ASAN (and UBSAN), the others should run the target with no sanitizers +compiled in. + There is also the option of generating a corpus using a non-ASAN binary, and then feeding it to an ASAN-instrumented one to check for bugs. This is faster, and can give you somewhat comparable results. You can also try using diff --git a/docs/power_schedules.md b/docs/power_schedules.md index cdada0f6..c69c64d2 100644 --- a/docs/power_schedules.md +++ b/docs/power_schedules.md @@ -20,6 +20,7 @@ We find that AFL's exploitation-based constant schedule assigns **too much energ | `-p lin` | 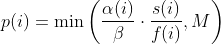 | | `-p exploit` (AFL) | 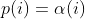 | | `-p mmopt` | Experimental: `explore` with no weighting to runtime and increased weighting on the last 5 queue entries | +| `-p rare` | Experimental: `rare` puts focus on queue entries that hit rare edges | where *α(i)* is the performance score that AFL uses to compute for the seed input *i*, *β(i)>1* is a constant, *s(i)* is the number of times that seed *i* has been chosen from the queue, *f(i)* is the number of generated inputs that exercise the same path as seed *i*, and *μ* is the average number of generated inputs exercising a path. More details can be found in the paper that was accepted at the [23rd ACM Conference on Computer and Communications Security (CCS'16)](https://www.sigsac.org/ccs/CCS2016/accepted-papers/). diff --git a/docs/status_screen.md b/docs/status_screen.md index 0bc636c4..8b3d5bda 100644 --- a/docs/status_screen.md +++ b/docs/status_screen.md @@ -372,26 +372,38 @@ For unattended operation, some of the key status screen information can be also found in a machine-readable format in the fuzzer_stats file in the output directory. This includes: - - `start_time` - unix time indicating the start time of afl-fuzz - - `last_update` - unix time corresponding to the last update of this file - - `fuzzer_pid` - PID of the fuzzer process - - `cycles_done` - queue cycles completed so far - - `execs_done` - number of execve() calls attempted - - `execs_per_sec` - overall number of execs per second - - `paths_total` - total number of entries in the queue - - `paths_found` - number of entries discovered through local fuzzing - - `paths_imported` - number of entries imported from other instances - - `max_depth` - number of levels in the generated data set - - `cur_path` - currently processed entry number - - `pending_favs` - number of favored entries still waiting to be fuzzed - - `pending_total` - number of all entries waiting to be fuzzed - - `stability - percentage of bitmap bytes that behave consistently - - `variable_paths` - number of test cases showing variable behavior - - `unique_crashes` - number of unique crashes recorded - - `unique_hangs` - number of unique hangs encountered - - `command_line` - full command line used for the fuzzing session - - `slowest_exec_ms`- real time of the slowest execution in seconds - - `peak_rss_mb` - max rss usage reached during fuzzing in MB + - `start_time` - unix time indicating the start time of afl-fuzz + - `last_update` - unix time corresponding to the last update of this file + - `run_time` - run time in seconds to the last update of this file + - `fuzzer_pid` - PID of the fuzzer process + - `cycles_done` - queue cycles completed so far + - `cycles_wo_finds` - number of cycles without any new paths found + - `execs_done` - number of execve() calls attempted + - `execs_per_sec` - overall number of execs per second + - `paths_total` - total number of entries in the queue + - `paths_favored` - number of queue entries that are favored + - `paths_found` - number of entries discovered through local fuzzing + - `paths_imported` - number of entries imported from other instances + - `max_depth` - number of levels in the generated data set + - `cur_path` - currently processed entry number + - `pending_favs` - number of favored entries still waiting to be fuzzed + - `pending_total` - number of all entries waiting to be fuzzed + - `variable_paths` - number of test cases showing variable behavior + - `stability` - percentage of bitmap bytes that behave consistently + - `bitmap_cvg` - percentage of edge coverage found in the map so far + - `unique_crashes` - number of unique crashes recorded + - `unique_hangs` - number of unique hangs encountered + - `last_path` - seconds since the last path was found + - `last_crash` - seconds since the last crash was found + - `last_hang` - seconds since the last hang was found + - `execs_since_crash` - execs since the last crash was found + - `exec_timeout` - the -t command line value + - `slowest_exec_ms` - real time of the slowest execution in ms + - `peak_rss_mb` - max rss usage reached during fuzzing in MB + - `afl_banner` - banner text (e.g. the target name) + - `afl_version` - the version of afl used + - `target_mode` - default, persistent, qemu, unicorn, dumb + - `command_line` - full command line used for the fuzzing session Most of these map directly to the UI elements discussed earlier on. |
